One of the best sets of security features for Windows is within the ASR rules, which consist of multiple security mechanisms within Windows.
You can read more about ASR at https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/overview-attack-surface-reduction?view=o365-worldwide.
These features include the following:
Application control – This restricts applications and code that can run in the system kernel. It can also block unsigned scripts such as PowerShell scripts.
Controlled folder access – This blocks untrusted applications to access protected folders.
Network protection – This blocks outbound HTTPS traffic that tries to connect to a known malicious source (based on the domain or hostname) based on Microsoft SmartScreen’s reputation.
Exploit protection – This applies multiple mitigations to ensure processes are not able to utilize exploits such as spawning child processes on the machine.
Device control – This allows us to prevent read or write access to removable storage.
What is Attack surface reduction (ASR) ?
Attack surface reduction (ASR) refers to a group of capabilities that reduce the attack surface of your devices by limiting their known areas of weakness.
ASR capabilities minimize the risk your device faces against threats such as zero days, exploits, and unauthorized activity.
Understanding ASR rules
ASR rules restrict system behaviors often used by attackers, whether the intent is malicious or not.
ASR Rules Modes:
Audit mode (2)
Block mode (1)
Warn mode (6)
ASR Rules
You can exclude folders and files from ASR rules, including those with wildcards and variables.
ASR rules require Microsoft Defender for Anti-Virus (MDAV) to be in Active mode with Cloud-delivered protection enabled.
ASR rules is they do what it says on the tin. Each ASR rule has a descriptive name and a GUID.
Standard protection rules
Block credential stealing from the Windows local security authority subsystem (lsass.exe) (9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2)
Block abuse of exploited vulnerable signed drivers (56a863a9-875e-4185-98a7-b882c64b5ce5)
Block persistence through WMI event subscription (e6db77e5-3df2-4cf1-b95a-636979351e5b)
Other rules
Block Adobe Reader from creating child processes (7674ba52-37eb-4a4f-a9a1-f0f9a1619a2c)
Block all Office applications from creating child processes (d4f940ab-401b-4efc-aadc-ad5f3c50688a).
Block executable content from email client and webmail (be9ba2d9-53ea-4cdc-84e5-9b1eeee46550)
Block executable files from running unless they meet a prevalence, age, or trusted list criterion (01443614-cd74-433a-b99e-2ecdc07bfc25)
Block execution of potentially obfuscated scripts (5beb7efe-fd9a-4556-801d-275e5ffc04cc)
Block JavaScript or VBScript from launching downloaded executable content (d3e037e1-3eb8-44c8-a917-57927947596d)
Block Office applications from creating executable content (3b576869-a4ec-4529-8536-b80a7769e899)
Block Office applications from injecting code into other processes (75668c1f-73b5-4cf0-bb93-3ecf5cb7cc84)
Block Office communication application from creating child processes (26190899-1602-49e8-8b27-eb1d0a1ce869)
Block process creations originating from PSExec and WMI commands (d1e49aac-8f56-4280-b9ba-993a6d77406c)
There is a variance in ASR rules regarding the generation of alerts in Microsoft 365 Defender or toast notifications to the user (if enabled). For any alerts to come to Microsoft 365 Defender, cloud-delivered protection (also known as the file blocking level) must be at least High. For a matrix of when alerts or user notifications are generated, refer to Microsoft’s documentation at:
Deploying ASR rules
ASR rules can be deployed using:
Intune
Group Policy
Configuration Manager
Intune:
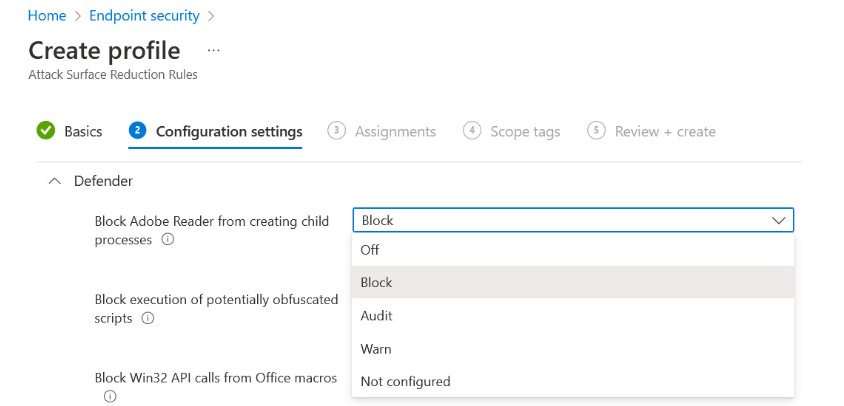
ASR rules are best managed using Intune by creating an Attack Surface Reduction rules profile via Endpoint security | Attack surface reduction | + Create Policy | platform of Windows 10 and later | profile of Attack Surface Reduction Rules.
Figure 1 – Configuring ASR rules in Intune
Note: Windows Servers ASR policy can be configured using Intune if the integration is configured between Intune and Microsoft for Endpoint.
Configuration Manager
If you’re managing ASR rules with Configuration Manager, follow these steps:
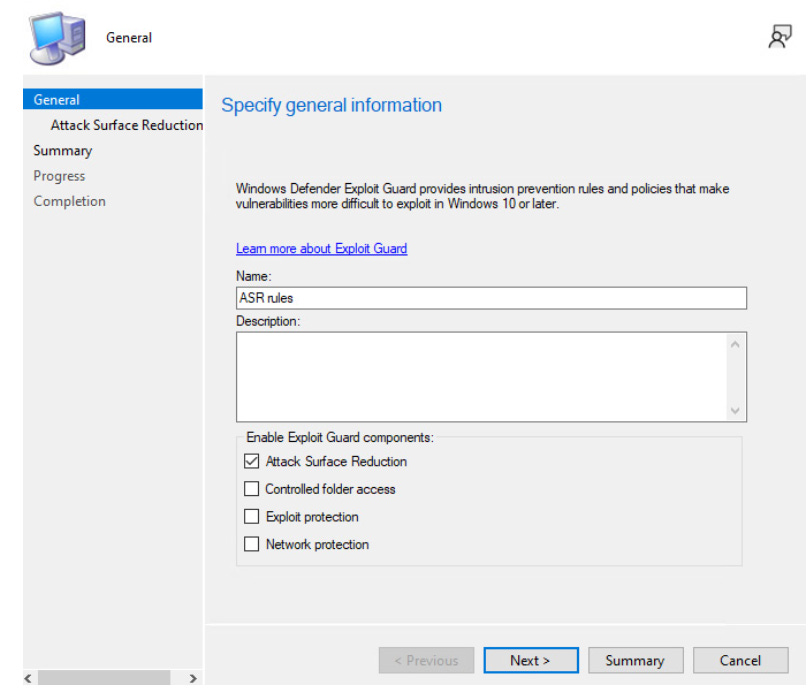
In the console, navigate to Assets and Compliance | Endpoint Protection | Exploit Guard | <your new or existing policy>.
Each policy can have several Exploit Guard components. Select, at a minimum, Attack Surface Reduction:
Figure 2 – Creating an Exploit Guard policy in Configuration Manager for ASR rules
Group Policy
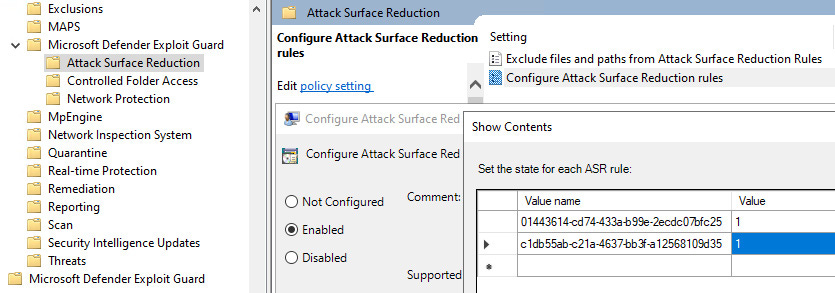
Group Policy objects can deploy ASR rules within Computer Configuration | Policies | Administrative Templates | Windows Components | Microsoft Defender Antivirus | Microsoft Defender Exploit Guard | Attack Surface Reduction.
When the Configure Attack Surface Reduction rules setting is enabled, you must also configure a list of value names (ASR rule GUIDs) and values (enforcement mode). These GUIDs can be found in the ASR rules overview section, and the values available (if supported for the rule) are as follows:
0: Off
1: Block
2: Audit
5: Not configured
6: Warn:
Figure 3 – Setting ASR rules in a Group Policy Object
Testing ASR Policy
Once you have applied the ASR profile, it can take some time before the test client syncs the new rules. You can also force the device to connect and download the latest configuration updates using one of the methods listed here: https://docs.microsoft.com/en-us/mem/intune/user-help/sync-your-device-manually-windows.
Once the device has been fully synchronized, we need to test that the ASR rule is working as intended. An effective way to test this is using the ASR testing tool from Microsoft, which can be downloaded from https://demo.wd.microsoft.com/Page/ASR2.
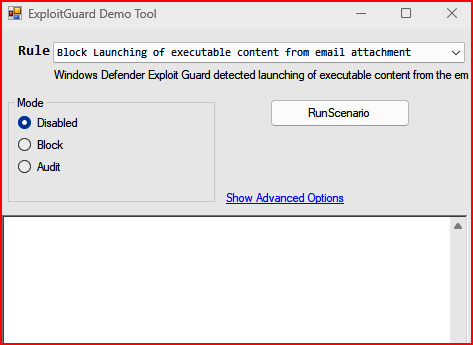
This provides built-in test scenarios that can be run directly from the client, as shown in the following screenshot:
Figure 3: The Exploit Guard Demo Tool configuration
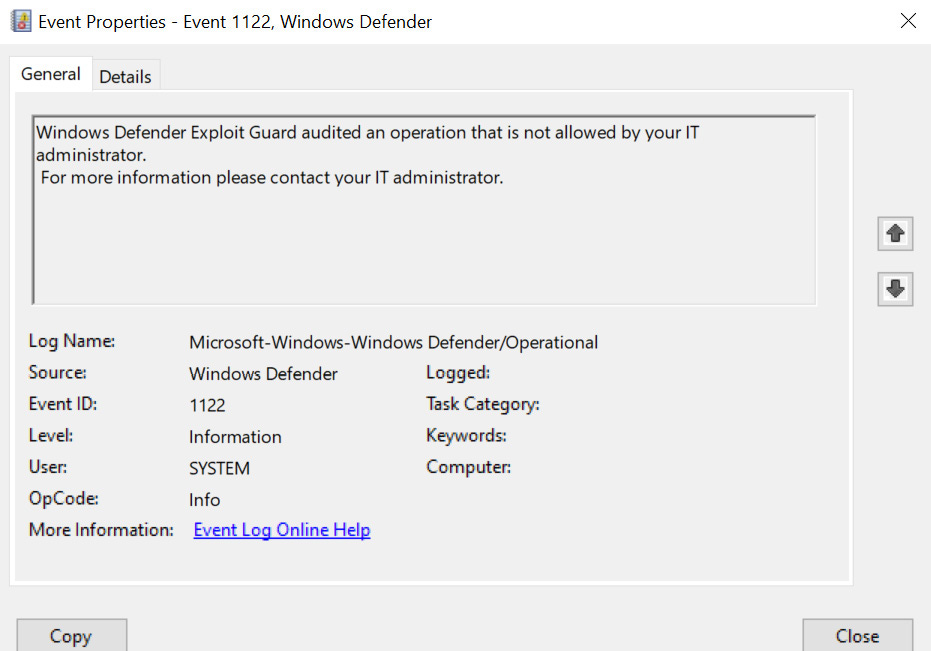
Here, if you run one of the following scenarios, such as Block creation of child process by Office application, it should trigger an event that will be generated under Microsoft-Windows-Windows Defender/Operational with an EventID value of 1122, where it says Microsoft Defender Exploit Guard audited an operation that is not allowed by your IT administrator, as shown in the following screenshot:
Figure 4 – Exploit Guard Event ID
Monitoring ASR rules
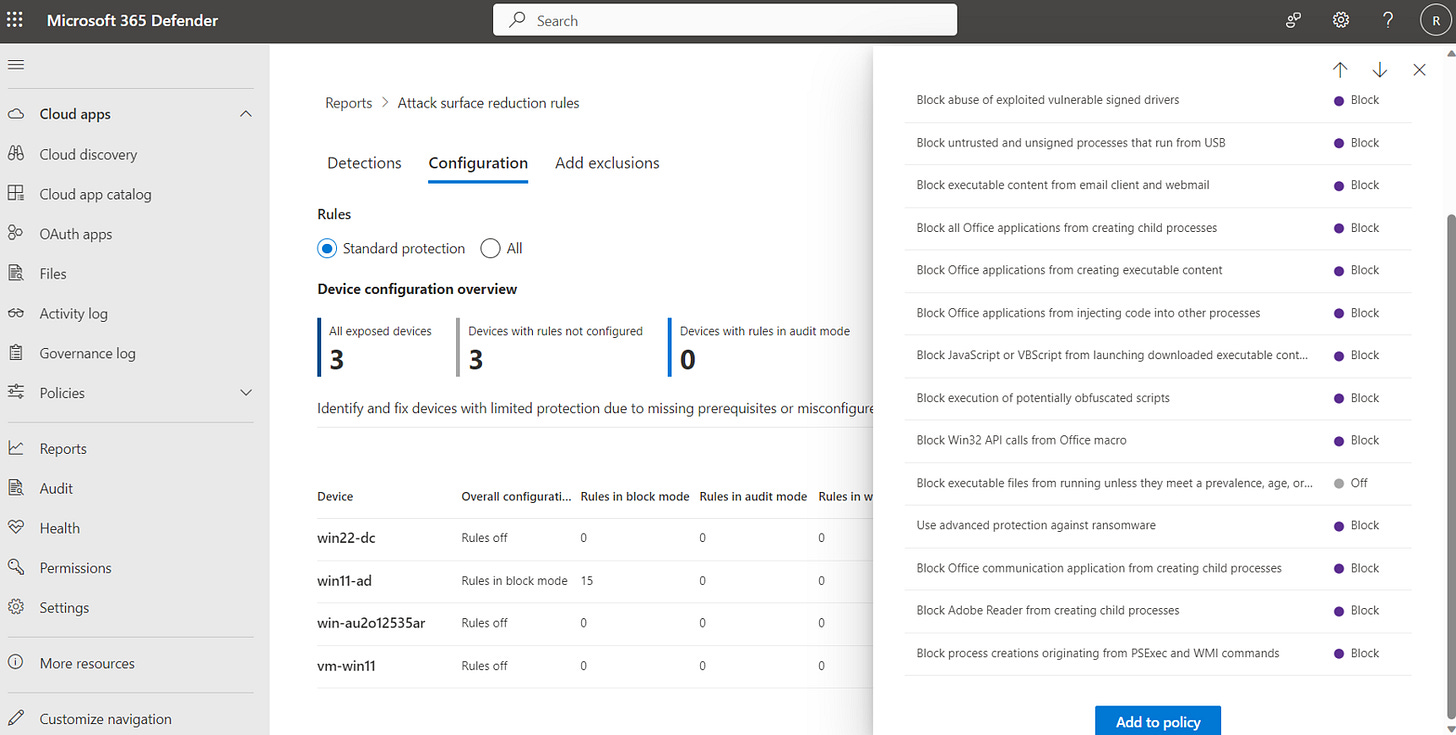
A good starting point is Microsoft 365 Defender | Reports | Attack surface reduction rules. This is broken down into three sections: Detections, Configuration, and Add exclusions:
The Detections tab reports ASR rule events, with filter options to view specific rules, and grouping options to choose how it is represented.
Figure 5: ASR configurations by device as viewed in the Microsoft 365 Defender portal
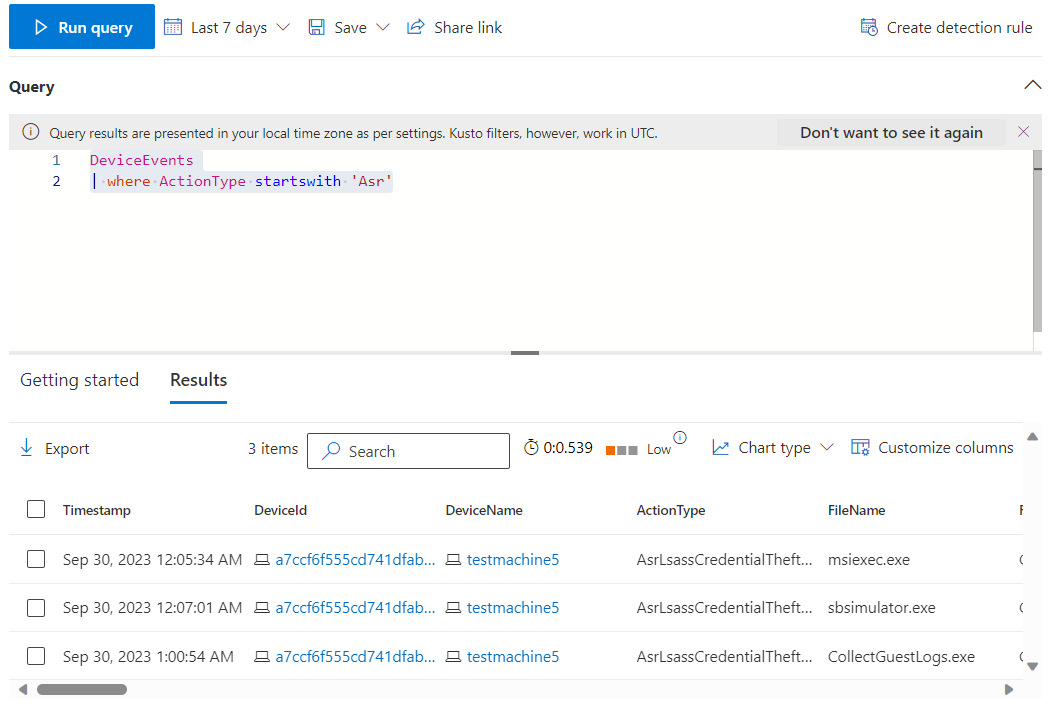
Advanced hunting also surfaces ASR events (limited to the first per hour for a device). Each ActionType for ASR rules begins with Asr. As an example of reviewing them, Microsoft provides the following query to see the total of each event:
DeviceEvents
| where ActionType startswith 'Asr'